Key messages from BR webinar Delivering the Promise of IoT at the Edge with Out-of-the-Box Connectivity

Presenters: Robin Duke-Woolley, CEO, Beecham Research; Olivier Pauzet, VP of Product & IoT Solutions, Sierra Wireless; Ohad Peled, Product Marketing Manager, Sony; Bee Hayes-Thakore, Senior Director Marketing & Partnerships, Kigen.
Watch nowAfter introducing the presenters, Robin outlined the state of the market and various market research findings. The growth forecast is huge, CAGR is variously estimated to be between 40 and 60%. He covered the different definitions of ‘Edge’; they depend on the different perspective of the value chain, e.g. user edge and service provider edge. They all involve local processing and minimising latency. The intelligent edge has been enabled by advances in chipset technology. The results on various surveys and interviews were summarised. Conclusion: IoT at the Edge is a game changer.

Sony’s presentation started by indicating how edge computing is shifting the balance of IoT solutions towards the edge.
While there are different definitions of the edge it is clear that the direction is towards computing power being distributed around the end-to-end solution components. The cloud used to do the heavy lifting, the processing, and devices sent data at frequent intervals. Today the devices and edge hardware have more computing resources, enabling them to process the data, which results in a more balanced solution. This balance is reflected in edge computing handling more applications in the edge devices. There is no need to send raw data to the cloud in order to enable apps such as preventative maintenance. Actions are initiated by the cloud when certain thresholds are exceeded.
The key advantages of edge computing are: less bandwidth is needed; the cloud gets more concise information so it can make faster decisions; costs are lower because lower power protocols like NB-IoT can be used as well as simpler modems. In addition devices can take autonomous decisions; security is enhanced because less data is sent to the cloud and security elements can be built into the chipsets; battery life is higher because less data is transmitted.
Finally, Ohad wrapped it up with an annotated visual of the Sony ALT1250, which is a fully featured system on a chip (SoC) that incorporates all the key components needed to build IoT applications. They include the MCU (microcontroller unit), a cellular modem that provides low-power LTE-M and NB-IoT protocols, and a hardware based iSIM, that stores network credentials and sits inside a secure element within the SOC. (274 words.)
Kigen’s presentation started by focussing on security, the need to integrate security into IoT devices, functionality that the company provides to its silicon ecosystem, which includes Sony and Sierra. Security is key to providing smart, data-based business decisions. They are enabled by employing compact, complex processing deployed at the thin edge of the network, the one that is close to the devices. Key security trends include iSIMs and chip-to-cloud security using GSMA’s IoT SAFE mechanism.
Bee recalled the fact that devices used to sense behaviour in their ambient environment, but the intelligent edge enables them to report on critical events in real time. For example, a smart packaging solution would indicate that there had been an incident such as a fall or a change in temperature as well as the location.
The edge is becoming an increasingly critical part of smart data infrastructures and the role of security can be distilled down to three tenents. One, the raw “little’ data generated by devices has to be secure and trusted. Two, secure-at-source data supports energy-efficient compute at the edge. And three, a secure edge facilitates the integration of the ML and AI capabilities needed for efficient processing.
The presentation concluded with an overview of the SIM, the component that stores identity securely, enables out-of-the-box connectivity, and acts as a root of trust. It has evolved from the removable 25 x 15 mm SIM used in smart phones; the form factor was not suitable for the constrained resources of IoT devices. The eSIM is much smaller, dimensions are 6 x 5 mm, and enhanced remote provisioning capabilities have been added. Now we have iSIMs which are 98% smaller than eSIMs. They are embedded in fully integrated chipsets, as covered by Ohad. In addition there is a significant reduction in the bill of materials.
Bee then outlined how iSIMs protect IoT data from chip to multi cloud. This is a key enterprise requirement. Data streams need to be protected from the place of collection all the way to the cloud. This is realised by leveraging GSMA IoT SAFE. (345 words).
The presentation of Sierra Wireless started by covering the complexity of connecting the IoT to the cloud. Device and connectivity management are required, there are various operation and technical challenges, embedded software experience is needed, as well as cybersecurity and telecommunications expertise. Costs must be predicted and IoT solutions need to work for several years. These issues should be simplified.
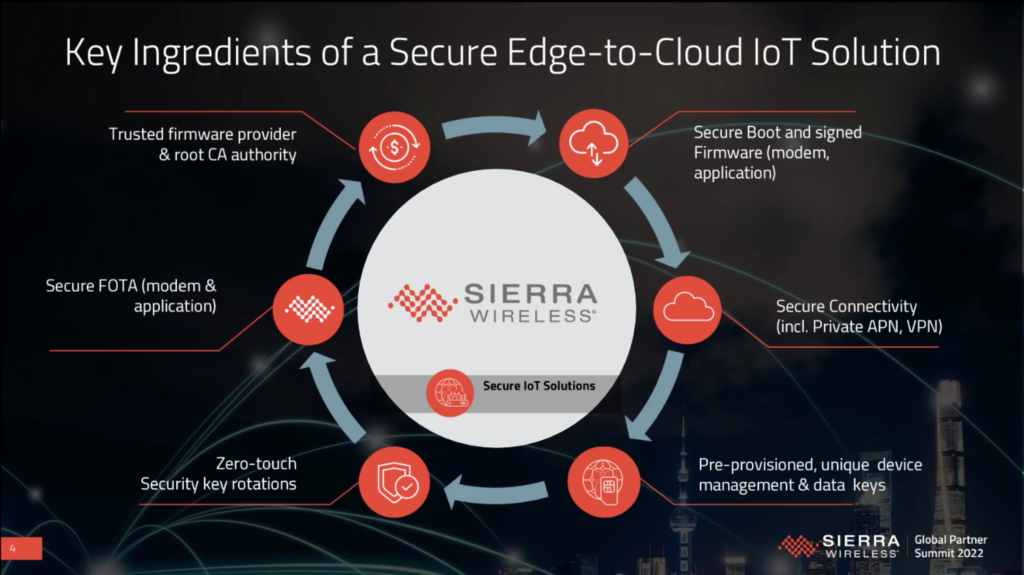
Olivier then moved on to security at the edge, which is a serious concern for the market.
Requirements include: a secure boot, hardware security modules, encryption, key management, OTA updates plus provisioning and managing large deployments. Everything needs to be addressed in order to provide out-of-the-box connectivity. Security is not rocket science, best practices should be followed. Connectivity at the edge involves a service spectrum that ranges from Cat-M/NB-IoT through to 4G LTE and 4G LTE-A and on to 5G NR. The associated software includes secure firmware over the air, secure device management and secure data management.
Sierra aims to make everything as simple, scalable and secure as possible. Simple involves speeding up development times and simplifying integration complexity. This is enabled by a rich set of edge and cloud APIs. Scalable is realised by designing products for longevity and employing the latest innovations. The company has been a trusted partner for 25+ years. Security was outlined earlier but it is worth noting that it involves security experts driving standards and best practices.
The webinar concluded with a short question and answer session.
Watch the full webinar on-demand here.

Bob Emmerson
Technology Editor, Beecham Research.
